19 June 2023

Globe, one of the largest mobile network operators in the Philippines with almost 90 million subscribers, was targeted by cyber criminals executing an intensive financial SMS phishing campaign.
SMS phishing messages were arriving from both international and domestic operators, impersonating real sources, using plausible sender information as well as regular local phone numbers. Many of these messages resembled real bank messages and most used malicious URLs to entice victims to visit fake bank webpages.
Spam polymorphism (changing the attack to avoid detection and blocking) was used extensively for these attacks. Techniques ranged from subtly changing key words, adding unnecessary spaces, including special characters, using tokenisation, duplicating letters to frustrate word-based fingerprints, to more visible ones such as replacing numbers and punctuation with text. Also observed was URL Cycling Detection, where criminal senders dynamically change the URL domain through a large set of temporary sites – which is used by criminals to avoid detection or blocking of their messages by slow response firewall updates.
In addition to frequently changing the SMS text body and URLs, an additional challenge to dealing with these threats was that the hosts of the attack websites used in that campaign had little in common, i.e., there was no correlation between the host IPs of the URLs being used.
Globe already had in place Enea AdaptiveMobile’s Network Protection Platform (NPP) for Messaging and Signalling Protection, which captured and handled the messages.
A sophisticated solution
Defensive techniques using a limited number of methods would be ineffective given the frequency and extent of changes by the attackers. No rules could work effectively against this campaign based solely on sender, URL, hosted IP, or text body.
Therefore, Enea AdaptiveMobile Threat Intelligence Unit (TIU), using the sophisticated and dynamic rules capability of the AdaptiveMobile NPP, developed and then applied a blend of security methods to address and control these attacks. TIU followed text pattern-based rules to manage the phishing attack campaign, along with other proprietary techniques, to capture the identified phishing messages.
The success and impact were reinforced by Globe’s chief information security officer Anton Bonifacio, who described the blocking of malicious messages as a “major step that reflects our commitment to the country’s economic recovery by ensuring that the accelerated digital adoption does not expose customers to worsening cyber threats.”
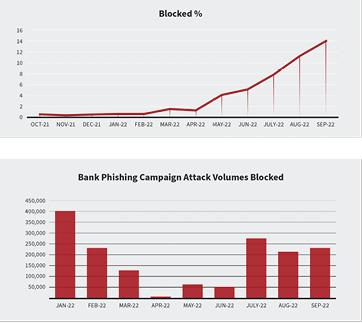
Enea AdaptiveMobile Security TIU along with the NPP Messaging Security platform has now successfully been blocking these phishing attacks over the last year. From January to April, the criminals were thwarted, moving away from Globe, and targeting other networks instead.
However, blocked threat messages increased considerably over the last few months, July to September. This was a result of more frequent updates being taken from Enea AdaptiveMobile’s managed Threat Intelligence service, contributing significantly to the effectiveness of the solution and allowing Enea to maintain detection and blocking rates even in the face of heightened volume and tactics of attackers.
Including these phishing attacks with all the other messages AdaptiveMobile NPP is blocking on Globe’s network - other scam campaign messages and grey route messages - there has been a significant impact over the past year. The level of protection afforded by the NPP to Globe’s customers has been critical in keeping them safe and protecting Globe’s brand and reputation as a secure mobile communications provider.
“The protection of our subscribers is at the heart of Globe’s cybersecurity strategy. Enea AdaptiveMobile Security understands that, and their strong cybersecurity background and intelligence allow them to go above and beyond in order to protect our network against both signalling and messaging attacks through their NPP,” said Bonifacio.
Globe’s next step was to apply strict rules to messages on domestic traffic, to target any person-to-person (P2P) messages containing URLs, without impacting commercial application to person messages (A2P).







